This article has 632 words.
What is phishing?
Phishing is a term used to describe the most widespread and effective methods of accessing other people’s information, mainly via the Internet. The term itself is a combination of two words - “fishing” (fishing) and “phreak” (telephone impulse thief). The part that says to fish is taken literally and means fishing for prey or data using electronic “bait”, “hooks” in an obvious and apt metaphor for the act itself. A further part of the term is a nod to the pre-Internet practice of hacking phone systems, known as “phreaking” and used by individuals called “phreaks” (Selby & Vescent, 2017).
Phishing occurs when a person impersonates another legal entity, uses emails or websites websites to obtain personal information about others. Phishers (people engaged in phishing) pretend to be banks, public institutions, online auctions, popular websites of all kinds and try to gain access to sensitive information such as bank account numbers, credit card numbers, passwords, detailed personal information, etc. Such emails ask potential victims to follow a link or call a number phone number in order to update their data, unlock their account, make payments, learn new important information, solve a problem that concerns us, or most simply are an attractive promotion or information that makes us curious (Marcum, 2015). For example, a phisher may send an email impersonating a impersonating Wells Fargo or Citibank, asking the customer to send account numbers and passwords to verify their status and data. He or she may pose as a university system administrator asking for an email password, in order to in order to complete the enrollment process.
One of the reasons why phishing attacks have become popular, and why they are increasing in number every year, is the the ease with which they can be carried out. DIY tutorials and ready-made scripts available on the Internet allow virtually anyone to prepare this type of attack. In a simple way, users can conduct a a phishing campaign and send out dozens or hundreds of emails that look like official notifications from, for example, UPS, DPD or InPost. In addition, they can appear as Facebook or Tweeter messages. Many webmail users do not bother to check the authenticity of each such message, because they assume that they come from legitimate entities and thus allow themselves to be “caught.” The most popular categories of phishing messages are shown in the chart below.
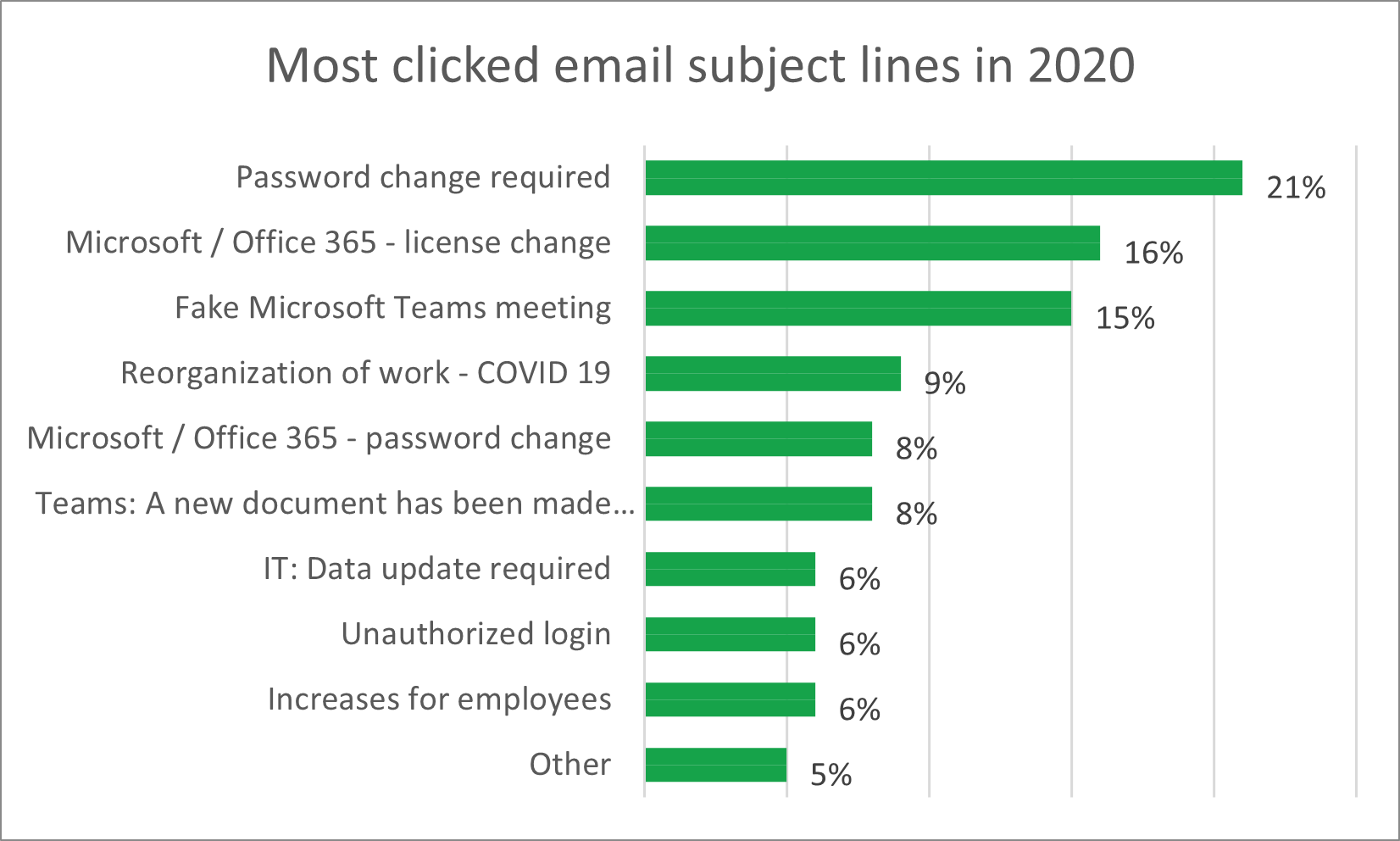
Types of phishing
Phishing can be divided into several categories. Each involves sending messages via email e-mail, but the way it is carried out sometimes differs, as does the purpose of the attack itself.
| Type | Description |
|---|---|
| Classical phishing | Theft of information, passwords, personal data through fake websites or malware. The goal is to get as much data as possible from the largest possible group of users. |
| Spearphishing | A variation of phishing that involves designing attacks into small, specific groups. This is done by highly personalizing the messages sent, which are created based on hours or weeks of observation of the victims. |
| Whale phishing | This is a development of spearphishing, in which the target of the attack is a high-profile person, such as a CEO (chief executive officer) or celebrity. Because of their popularity, the positions are called “big fish” or “whale,” which is where this type of phishing originated from. |
| Catphishing | Phishing that involves impersonating virtual personalities, building a relationship with the victim and attempting to gain access to financial data or sensitive information that the victim will share under the influence of trust. |
| Vishing / smishing | This is phishing that targets phone users and takes place via voice or SMS messages. |
Bibliography
- Marcum, C. D. (2015). Cyber Crime. Wolters Kluwer Law & Business.
- Selby, N., & Vescent, H. (2017). Cyber Survival Manual: From Identity Theft to The Digital Apocalypse and Everything in Between. Weldon Owen.